Bybit's $1.4bn Hack
The largest ever hack in crypto
TLDR:
Bybit was hacked for $1.4bn last week, representing the single largest hack ever in cryptocurrency history, with over 400,000 ETH being stolen.
The hack was done by having the internal Bybit team sign a transaction from their cold wallet multi-sig that appeared to be normal but was actually malicious.
Zachxbt the crypto-crime investigator quickly tracked down the culprits to be the infamous North Korean state-funded hackers called the Lazarus Group.
Bybit have done an incredible job in handling the hack and no individuals lost their money, yet other exchanges haven’t done so well in the past.
To stay safe from exchnage hacks like this you should self-custody your funds. Remember the old addage: “not your keys, not your coins”.
Last week we had the largest ever hack in crypto as the centralised exchanged Bybit was hacked for $1.4bn!
This week I decided to dive into how this hack happened, who was behind it, and what’s come out of it.
If this post resonates with you and you want to continue the conversation then jump in here: beginners.tokenpage.xyz
This newsletter goes out weekly to almost 10,000 subscribers. Please message me if you’re interested in sponsorships or partnerships.
Watch the Video version of this Post
ByBit Hack
ByBit is the second largest centralised exchange (CEX) in crypto by trading volume, with approximately 9% market share last year they are second only to Binance with it’s huge 39% market share.
Bybit have been around since 2018 and are predominantly based in Dubai and Singapore. In just a few short years they’ve become a real powerhouse in the space.
Last week, on February 21st 2025, Bybit suffered the largest ever hack seen in crypto history with approximately $1.4bn being stolen from one of their cold wallets!
The hack represented around 10% of their total $15bn reserves at the time! Since then there have been billions of dollars withdrawn from the exchange, and now they only hold around $11.4bn according to DeFiLlama.
Given the extreme circumstance the company’s done incredibly well, having been able to keep up with the withdrawals and stay solvent!
Their CEO Ben Zhou has been praised by many in the space for handling the situation incredibly well given the insane size of the hack.
So what happened?
The Hack
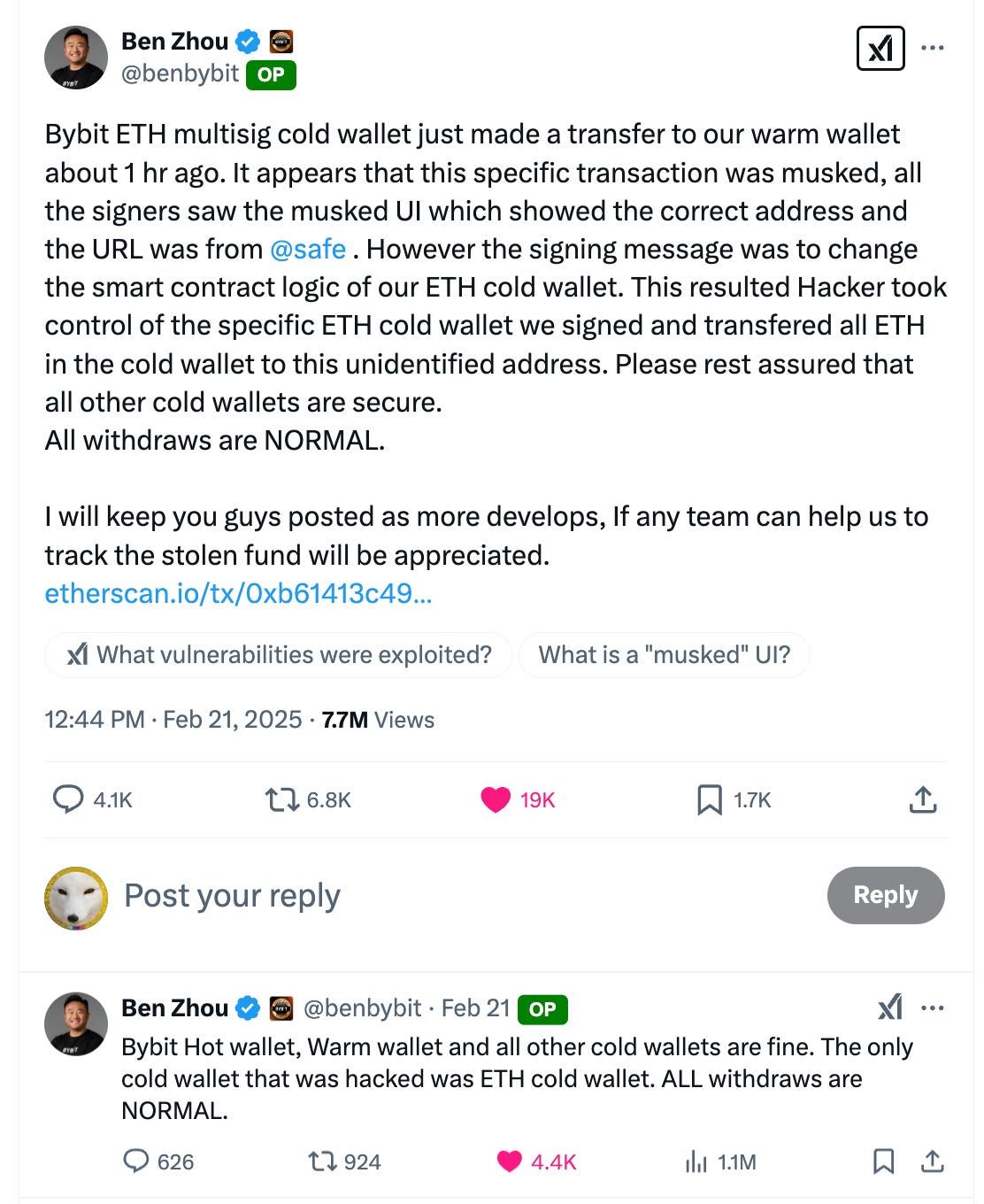
Ben Zhou explained in an X post that the hack was orchestrated through one of their cold wallets. The hackers essentially fooled the Bybit team to sign a transaction that took control of their wallet and then transferred all their funds out, around 400,000 ETH and a bunch of ERC20 tokens that amounted to around $1.4bn.
To understand what happened it’s important to have an idea of how CEXs work in general.
All CEXs have some sort of split of their funds between hot/warm wallets that are used at a high frequency to handle deposits and withdrawals, versus cold wallets that are more secure and therefore used to hold larger amounts of money and interact with less frequently.
It seems that in this case one of their cold wallets that was designed to be super secure and held a bunch of ETH, was doing a routine transaction sending some ETH over to a warm wallet probably to rebalance the ETH between different wallets.
This specific cold wallet was a Safe MultiSig, which I’ve written about before. Multisigs provide added security to a cold wallets because they require several private keys to sign to confirm a transaction.
You can imagine that the internal Bybit team were just running a pretty normal transaction and appeared to have some version of the Safe multi-sig UI above where it was performing a transaction they were used to seeing. It would have all looked the same as usual from their side.
However, the hackers had somehow gotten access to this interface and masked the real transaction that was happening, namely one that gave the hackers full control of that Ethereum multi-sig!
Once this transaction was signed it was already too late, the hackers got full control of the wallet and transferred out over 400,000 ETH in a single transaction to their own address, as well as sweeping lots of other ERC20 tokens.
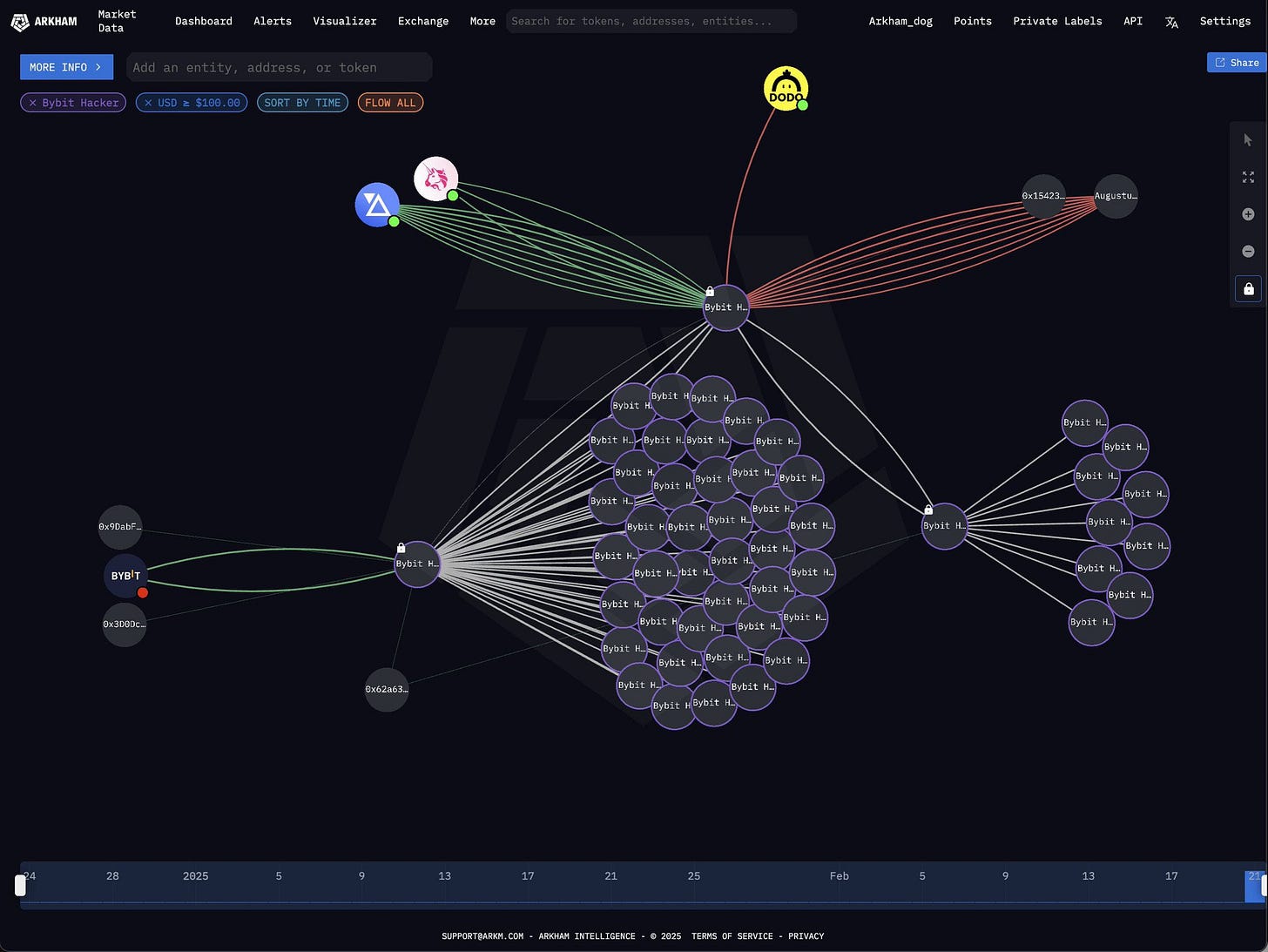
The hackers then went on to rapidly spread out this 400,000 ETH into tens of other wallets in 10,000 ETH amounts.
In the image above you can see the Bybit Hacker address bubble interacting with tens of other addresses as they sent 10,000 ETH to each one.
Luckily no other Bybits wallets were affected by the hack, and Bybit been able to maintain wihdrawals going without the CEX running out of money!
So who was resposible for this?
Lazarus Group and Zachxbt
Zachxbt is one of the most well known crypto-crime investigators in the space - although nobody knows who he really is.
And as soon as a bounty was created by Arkham Intelligence to find the criminals through their platform, Zachxbt quickly solved the crime by linking the criminals’ addresses to previous addresses used by the Lazarus Group.
Since then the hacked funds have been comingled with funds from other previous hacks performed by Lazarus, showing it’s definitely them.
But who are the Lazarus Group?
Well, they are an infamous group of hackers from North Korea.
Yes, the country North Korea has a set of hackers that are funded by the government to commit cybercrime including by hacking cryptocurrency companies!
North Korea is a dictatorship led by Kim Jong Un, and one of the poorest countries in the world, so we can only imagine the hackers look something like this:
All jokes aside, Lazarus Group are the single largest crypto hacking group in the entire world - since 2017 they’ve stolen over $6bn of crypto worldwide! With most of the money supposedly going into funding the country’s nuclear weapons programs.
This Bybit hack was the single largest crypto hack ever, but Lazarus are also responsible for the second largest hack in crypto where they stole $600m from the Ronin chain. At this point they’ve racked up a significant number of high profile hacks.
What’s Next?
Since the hack Bybit have managed to keep things under control and manage the situation exceptionally well.
Even with all the withdrawals that happened immediately after the hack, they’ve held strong and even started paying off the temporarily loans that they were given by other big players in the space to cover the immediate hole in their balance sheet.
Their CEO Ben Zhou has personally declared war against the Lazarus Group creating the website lazarusbounty.com, which he hopes will incentivise people to block or recover some of the funds lost. Bybit are giving up to 10% of the funds recovered to those who find them.
Unfortunately this type of crime in crypto will continue. There’s no chance North Korea’s Lazarus Group will stop considering just how successful they’ve been in the past, and they’ve already started laundering these hacked funds as shown by Arkham Intelligence:
Given the situation, Bybit have dealt with the crime in the best way that anyone could possibly imagine and I applaud them for their hard work.
Unfortunately though it’ll always be the case that criminals will act in the space so as individuals we need to be super careful!
Luckily in this case ByBit are still solvent and making everyone whole, but in the past other CEX’s haven’t been able to and people have lost their own money through these types of hacks.
Around 2 years ago I wrote a long post on how to keep secure called Web3 Security 101 - so make sure to check it out if you haven’t already.
Crypto is well and truly still the wild west, if this can happen with such big players with a lot of money to spend on security then imagine the many ways ordinary people can get burned.
So always remember to self-custody where possible, following the old saying “not your keys, not your coins”.
Don’t be afraid to be in the space, just be aware and make sure to protect yourself!
Whenever you’re ready, these are the main ways I can help you:
FREE access beginners.tokenpage.xyz - Get a free video guide on how to set up your first wallet and buy your first crypto. Plus a 1-on-1 call with me for free, and $1,990+ of bonus course material.
VIP access beginners-vip.tokenpage.xyz - Get VIP access with me as I show you how to navigate crypto’s. Includes weekly Q&A calls where you can ask me anything, and our proprietary DeFi portfolio software.
Web3 software development at tokenpage.xyz - Get your Web3 products and ideas built out by us, we’ve built for the likes of Zeneca, Seedphrase, Creepz and more.