Web3 Security 101
Keys, Hot vs Cold wallets, Hardware wallets, Multi-sigs, Signing safely
TLDR:
Wallets hold keys, not coins or tokens - “not your keys, not your coins”
Hot wallet’s keys can be accessed through the internet, cold wallet’s keys cannot
Hardware wallets provide the best protection vs usability trade-off available today
Multi-sigs can be used as vaults for large values of slow moving assets
Careful signing transactions, use something like Pocket Universe to understand what you are signing
If you’ve been in Web3 and crypto for long enough, or even not that long at all, you’ve likely heard of many multi-million dollar hacks. From massive projects like Axie Infinity getting hacked for $615m to the random degen trader you met in some Discord server who lost his NFTs, hacks are all too common in Web3.
Even the most well informed people in the space can mess up, only a few weeks ago Kevin Rose signed a dodgy transaction and had over $1m worth of NFTs stolen.
The reason hacks are abundant in Web3 is because it is genuinely hard and confusing to secure your assets effectively. Bitcoin was created in 2008 meaning the entire crypto space is only 15 years old and it takes time for new tech’s security practices to mature. People are still used to the username and password paradigm but in Web3 it’s entirely different. There are all sorts of different attack vectors you need to be wary of plus when your wallet is drained there’s no recourse for getting assets back like in traditional finance where for example a credit card transaction can be reversed. Hackers know this and go to great lengths to prey on vulnerable people in the space.
As a participant in the space it’s important to really understand basic security practices to avoid malicious actors the best you can. Moreover as a project builder you may even have custody of other people’s tokens or the project’s money so you need to be even more secure. In this post I hope to give you the fundamental concepts and tools to be secure in Web3.
Understanding Keys
The first thing to understand is how wallets in Web3 actually work. Unlike real world wallets, in Web3 wallets don’t store your coins or tokens, instead wallets store the “keys” to access them! Hence the old adage in the space “Not your keys, not your coins”. But why are wallets storing keys and not coins?
To understand this you first need to understand private and public key pairs and for that you need to understand that cryptography underpins the entirety of this space, its why we use the term crypto-currency. Cryptography conjures up images of something sinister and illegal but in reality it’s used literally everywhere in computing and is an essential component of our modern world. In cryptocurrencies it’s used in many different ways, from facilitating mining to generating the addresses people store their coins in.
Private and public keys are a well established and regularly used concept within cryptography. Essentially you generate a pair of keys, one that’s private and only you know and one that’s public and anyone can know. You can picture the private key like a physical key itself while the public as the keyhole it opens. Anyone can view a keyhole but only someone with the key itself can open it. Public keys are therefore no big deal to share and anyone can know them, meanwhile the private key must always be kept private. If someone else gets a copy they can open the corresponding keyhole.
Bitcoin addresses were architected to be created from public keys, and all subsequent cryptocurrency networks have copied this model. A private and public key pairing is created, then the public key goes through a specific hashing function to create the address itself. The address format is slightly different though for every network, in Ethereum addresses are called “accounts” and look like this: 0x8e720F90014fA4De02627f4A4e217B7e3942d5e8
Private and public keys are nothing more than long sequences of numbers and letters connected by cryptographic functions (ie. by fancy maths). The example Bitcoin paper wallet above generated with bitaddress.org, has private key: L3HNtb8p1RzoEWEqbxvQBF23u8ZTnC1PPHQCDRVEhM2q5mJsy9kX, and address: 1hhEaXN12GkfpZyiP5LpGGFC6xxm2H83R. This address looks different to an Ethereum address but the underlying public key has the same format.
Mnemonic Seed Phrase
Private keys in their normal format are hard for the human brain to interpret let alone to remember. So back in 2013, BIP-39 (Bitcoin Improvement Protocol) introduced mnemonic seed phrases for the Bitcoin network, and the standard has been copied throughout the space since. Instead of long sequences of numbers and letters we use a sequence of words, which is far easier to memorise. The BIP-39 standard has a library of 2048 words, using at least 12 random words from this library you have enough bits to securely encode a private key.
We don’t generally just pick random words ourselves though because humans suck at being truly random instead we usually use programs for this. These mnemonic words map over to the original underlying sequence of numbers of letters that compose the private key itself.
The magic of seed phrases really comes to light when they are coupled with BIP-32’s “hierarchically deterministic” (HD) wallets. HD wallets are nothing more than a method to use one private key to generate infinite new private and public key pairs, and hence infinite new addresses. This is why for example when you use a wallet like Metamask you only need to create one seed phrase at the start to generate as many accounts as you want.
You might begin to ask yourself, how can we just keep generating private keys and not accidentally generate the same as someone else has in the past? Well in theory it’s possible, just like it’s possible for the world to randomly explode at any given moment, however the chances are so slim that for all intents and purposes its impossible. The number of possible private keys is 2^160, which is an absurdly large number. To give perspective that’s more than the number of atoms in the observable universe.
So wallets store keys (not coins) and these keys give you access to all of the assets stored in a corresponding address. So naturally you should NEVER share your keys with anyone! Any time you type those keys or seed phrase somewhere you are making a copy of them and risk having all your assets stolen. This includes typing them on a notepad app or any digital document. If you ever see a website asking you to type your seed phrase in you can be 100% certain it’s a scam.
Hot vs Cold wallets
Wallets can also be described in terms of being hot or cold. Remember once again that wallets hold onto keys, so it’s incredibly important to know how the wallet is storing and protecting the keys themselves.
Hot wallets are those where the keys are accessible via the internet. By being accessible through the internet hot wallets run the risk of keys being stolen, this is done as a trade-off for a much easier user experience.
One of the most used hot wallets in Web3 is Metamask, which not only acts as a wallet but also allows you to connect to dApps (decentralised apps) on Ethereum and other EVM compatible chains. When you create a Metamask wallet it will generate a seed phrase that gets saved in a hidden folder on your computer that it then uses to create accounts and sign transactions. If some malicious software makes itself onto your computer through the internet then it can potentially make a copy of those keys in the folder and with this copy steal all of your assets.
Cold wallets store keys such that they are not accessible via the internet. Cold wallets provide keys far more protection at the cost of being a lot less practical.
The most basic cold wallet is just a piece of paper that you’ve written your private keys on, we call this a paper wallet. Obviously pieces of paper cannot download malicious software and be hacked, so as long as the paper is hidden in a safe and secure place then your keys are safe. However, with a paper wallet the moment you need to access your funds you need to turn the wallet “hot” by copying the key into some wallet software. Nowadays we have hardware wallets though, which have elevated the standard of cold wallets to something that still keeps your private keys offline yet are a lot more user-friendly and usable than other cold wallets.
Hardware Wallets
Hardware wallets are probably the best compromise on security and usability you can have in crypto today. The way these work is that when you buy a new one, assuming it has not been tampered with, on initialisation you will generate an entirely new random seed phrase. Make sure to store the seed phrase securely on a paper wallet in case the device breaks or gets lost.
The hardware wallet itself has mini apps that can be downloaded and allow you to connect to different cryptocurrency networks. The hardware wallet will then use its seed phrase as a HD wallet to generate as many private keys and address pairs for each network you want, and most importantly sign transactions on the device itself.
On creating a transaction to submit to the network you need to sign with a private key, as with the earlier metaphor, the private key opens the keyhole proving you own that address. Signing with a hot wallet like Metamask happens within your computer, but with a hardware wallet it happens on the device itself and the keys never actually leave it. This is really crucial and where the main security benefit comes from as the keys never become accessible via the internet.
Nowadays with Metamask and other similar browser wallets you can select to “connect hardware wallet” so that you interact with dApps just like you would with Metamask as a hot wallet but all transactions are signed offline on the device. This process is still very cumbersome though even for more technical people in Web3, yet by doing this you reduce the risk of stealing your keys down to pretty much zero.
Moreover, if anyone malicious gets hold of the hardware wallet the likelihood that they steal your keys is still incredibly low because the device is pin protected. If you type the incorrect pin 3 times then the hardware wallet resets itself back to factory settings deleting the seed phrase entirely. You can then still access your funds again by re-typing the seed phrase into a new hardware wallet.
The two largest hardware wallet players in the space today are Ledger and Trezor. Both manufacturers’ devices work incredibly well and are highly recommended. Choosing between them is really down to personal taste on the UI and UX of their software and device itself. Its not so important which one you choose, what’s important is that you get one!
Multi-Sig Wallets
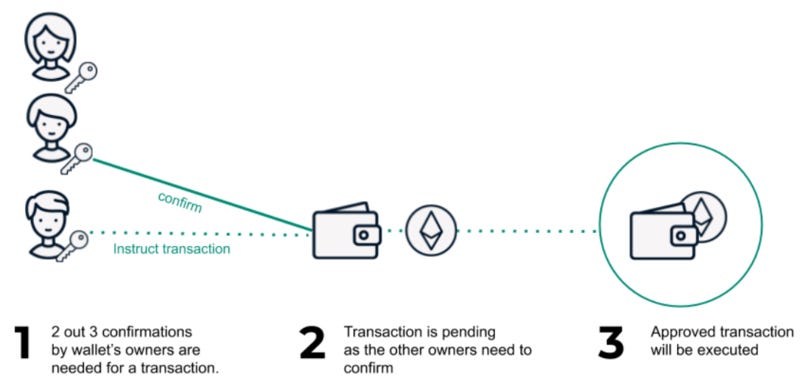
As a project owner it may even be best to go one step further and use a multi-sig. Multi-sig stands for multiple signatures as you need multiple keys to sign a transaction successfully. You can consider it as an added layer of authentication for a cold wallet just like 2-factor authentication is common on password protected apps.
Multi-sigs make it harder to access funds within an account because now you need multiple keys for a transaction. They usually come in all sorts of N-of-M combinations. For example a common variant would be a 2-of-3 multi-sig, where 3 keys are generated and held by 3 different users but only 2 of them are needed at any time for the transaction to be successfully signed.
Depending on the amount of money involved within a project it can be important to have a multi-sig vault where you store high valued assets that are unlikely to be moved frequently. Projects and people with a small amount of money at play may not need this, but if for example you release an NFT collection and sell out making over $1m from minters, it would be wise to protect that money with a multi-sig as its no longer just your money but its in fact your customers’ money too.
For Ethereum and other EVM chains the most recommended multi-sig provider is Gnosis Safe. Gnosis has become the de-facto standard for Ethereum and is regarded as best in class.
Signing Transactions
Now you are super secure with your keys themselves, the final thing to be careful with is the transactions you actually sign! The hack that happened with Kevin Rose that I mentioned at the start was not because anyone stole his keys, but rather that he accidentally signed a dodgy transaction that gave another account access to his NFTs.
Many people in this space are so worried about hacks that they even refuse to connect their wallets to websites they are unfamiliar with. Yet connecting a browser wallet like Metamask is never a problem in itself and is often important for the website to function properly. At worst malicious websites will be able to associate your IP with your Ethereum account - so don’t be scared to connect.
The problem comes in signing a dodgy transaction. Smart contracts can be written in all sorts of colourful ways that appear to be doing one thing but under the surface are doing something entirely different and malicious. When Metamask tells you about the transaction you are signing it will rarely give you any genuinely useful information.
However, new solutions have appeared to help combat this. The one I recommend the most is Pocket Universe, which is a browser extension that intercepts a transaction coming into a browser wallet like Metamask and simulates it to give you a better visual understanding of what it’ll do if you sign. Below is a comparison between both for a buying transaction on Opensea. The information on Metamask is pretty useless, whereas Pocket Universe gives a genuinely useful explanation that after the transaction you’ll have -0.733 ETH and +1 NFT.
Using a solution like Pocket Universe is almost a necessity nowadays as “Blind Signing” has become the norm. Those with a Hardware Wallet will likely have been asked to enable blind signing already. In essence when you blind sign you allow your device to approve a smart contract transaction without it displaying the full contract data to you. In other words, you’re agreeing to trust, instead of verify, the transaction. With Pocket Universe you still get a sense of what will happen before you sign though.
Another great solution that’s beginning to be implemented more is delegate.cash. This allows you to use a secondary account that’s been delegated to sign for your primary account, which takes away the risk of accidentally signing a dodgy transaction that will drain your primary account. However, it requires the smart contracts you interact with to implement the delegation mechanism, and ultimately you will still need to transact with your primary wallet from time to time, eg. when you want to trade NFTs.
Suggested Setup
Considering all of the above, there are many configurations that you can adopt either on a personal or project level.
The most basic setup that I think fits for most people regardless of whether they are running a project or just securing their own funds is as follows:
Metamask wallet (hot wallet)
→ Daily low value transactions, can set it up as a delegate for your ledger. This is like your real-world wallet that has limited cash for day-to-day usage.Ledger/Trezor wallet (cold wallet)
→ Holds most of your funds and NFTs that get used semi-regularly. This is like a bank account. Keys are safely stored, but you should still only sign transactions when you are certain of their origin, if you are uncertain use the hot wallet.Multi-sig vault (cold wallet)
→ Holds high value tokens and NFTs that you are unlikely to move regularly. This is like a bank vault for assets that don’t need regular access.
Kevin Rose’s setup after the hack is not too dissimilar, you can see in his tweet below.
There are many ways to secure your keys. An incredibly important thing is to not try and get too smart though. People will sometimes split their seed phrase into multiple pieces stored in multiple places and then lose one part and end up losing their keys forever. Know yourself and your own risks vectors to avoid doing something that sounds smart in theory but can backfire in practice. Use the tools that already exist as they are battle-hardened and have existed for a long time.
Security is an important topic so this post is quite long as its intended to give you all the core concepts needed to stay secure in Web3. Nonetheless, this is only scratching the surface as security is a rabbit hole in of itself.
Plus, security is also somewhat of a moving target because as the ways to protect yourself improve so do malicious actors find more innovative ways to break them. Nonetheless, understanding everything that’s been written here will give you the core tools you need to protect your personal and project assets well in Web3.